Cyber Security Alert: Snowflake Attack Impacts Cylance and Pure Storage

Tuesday 11th June 2024
Snowflake Attack Overview:
The Snowflake attack, also known as the UNC5537 attack, is a significant cybersecurity incident that has affected numerous Snowflake customers. It is linked to news released from Live Nation, who own Ticketmaster and who noticed suspicious activity on their account around 20th May. The Snowflake attack was carried out by a financially motivated cybercriminal group, tracked as UNC5537. The attack on Snowflake involved a malicious third-party that gained access to some of its customers' accounts and data through a compromised Snowflake employee account. The attacker was able to use the stolen credentials to create API keys and tokens, and then use them to impersonate the customers and access their data. The group is highly likely to have stolen a significant volume of records from Snowflake customer environments. The attackers obtained access to multiple organisations’ Snowflake customer instances via stolen customer credentials. These credentials were primarily obtained from multiple infostealer malware campaigns that infected non-Snowflake owned systems.
The attack led to the export of a significant volume of customer data from the respective Snowflake customer instances. The threat actor has subsequently begun to extort many of the victims directly and is actively attempting to sell the stolen customer data on recognised cybercriminal forums.
As many as 165 customers of cloud storage provider Snowflake have been compromised. Notably, none of the affected accounts made use of multifactor authentication. Cylance, Pure Storage, QuoteWizard and Live Nation were among customers notified they were affected in the incident. Pure Storage and Cylance were among the affected customers, as they used Snowflake's platform for data analysis and business intelligence.
There’s a realistic possibility the group behind the Snowflake intrusions may have ties to Scattered Spider, aka UNC3944 – the notorious gang behind the mid-2023 Las Vegas casino breaches.
Cylance Impact:
Cylance also confirmed that some of its data was exposed but did not specify what kind of data or how many customers were impacted. Both companies said they took immediate steps to secure their accounts and data, notifying the relevant authorities and customers.
The data allegedly belonging to Cylance is being sold on a crime forum, but the company has stated that this does not endanger customers. The data is said to be related to company marketing between 2015 and 2018, before BlackBerry acquired Cylance.
The alias selling Cylance’s data is called “Sp1d3r” and they claim 34 million customer and employee emails are included in the data dump, exposing personal information and other internal documents. The data is supposedly being sold for $750,000.
BlackBerry Cylance has stated that their systems and products remain secure and are being closely monitored by their security operations team. They also mentioned that based on their investigation to date, they do not believe that BlackBerry data and systems related to their customers, products, and operations have been compromised.
Pure Storage Impact:
Pure Storage, a secure storage company, confirmed that the attacker accessed some of its data hosted on Snowflake, including customer names, contact information, hashed passwords, and metadata. The compromised workspace contained “telemetry information” used to provide customer support services. The information includes company names, Lightweight Directory Access Protocol (LDAP) usernames, email addresses, and the Purity software release version number. Importantly, the workspace did not include compromising information such as passwords for array access, or any of the data that is stored on the customer systems.
Pure Storage emphasised that no customer data was compromised but has not specified how exactly the breach occurred. The breach is being linked to a lack of Multi-Factor Authentication (MFA), although this has not been confirmed. Pure Storage has stated that their wider infrastructure remains unscathed, and they are continuing to monitor customers’ systems. They have also engaged a leading cybersecurity firm to validate their findings.
Analyst Assessment:
It is difficult to assess the full impact of the Snowflake attack at present, as investigations are still ongoing. However, several key points can be highlighted:
- It is highly likely more robust cybersecurity measures, including the use of multi-factor authentication has helped Organisations who have these in place. It is highly likely this systematic attack targeted those Organisations who were perceived to have a weaker security posture, as these are almost certainly viewed by threat actors as easier targets.
- There is always a risk of using cloud-based platforms and services and it was only a matter of time until a cloud-based platform was breached. The Organisations which have strong security measures and are which monitor, prevent and detect unauthorised access are unlikely to be easy victims.
- There is a realistic possibility this supply chain attack can continue, as the extent of the attack is unknown, and it may be difficult to remove the Infostealer from networks. This means it is likely the attack will worsen or get bigger before it is stopped.
Please note that the situation is still developing and the information available is based on the latest reports. For the most accurate and up-to-date information, it’s best to refer to official statements from the company involved.
References:
- Ticketmaster confirms data breach and personal info lost, says Snowflake systems were hacked (msn.com)
- https://www.bleepingcomputer.com/news/security/pure-storage-confirms-data-breach-after-snowflake-account-hack/
- https://www.bleepingcomputer.com/news/security/cylance-confirms-data-breach-linked-to-third-party-platform/
- Cylance clarifies breach, dodges questions about the source • The Register
- Pure Storage, a secure storage company, recently confirmed a data breach related to a compromised Snowflake workspace
- https://blog.purestorage.com/solutions/achieving-cyber-resiliency-with-pure-storage-safemode/
- The attack was carried out by a financially motivated cybercriminal group, tracked as UNC5537
- https://www.theregister.com/2024/06/11/pure_storage_snowflake_breach/
- https://thecyberexpress.com/blackberry-cylance-nyt-breaches/
- https://www.theregister.com/2024/06/11/cylance_clarifies_data_breach_details/
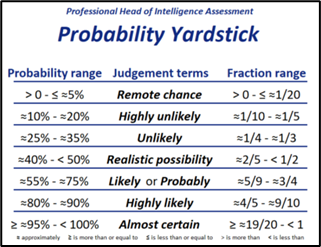
The Probability Yardstick
To quantify language, we use the Probability Yardstick from the Professional Head of Intelligence Assessment. It is a tool used in the UK Government to standardise the way we describe probability and has been used to ensure consistency across the different thematic areas and threats when providing assessments on how likely something is to occur. The yardstick is attached below for information.
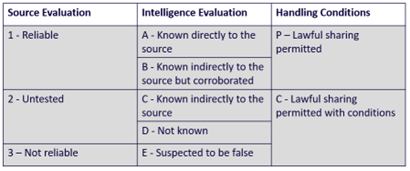
Source Evaluation:
We also assess our sources using the below matrix but rarely disclose our source, to protect its integrity. We assess sources on how reliable they are, how they accessed the intelligence, and we then decide if this intelligence can be shared. The below table illustrates this:
Confidence Levels:
|
High Confidence |
High confidence generally indicates judgements based on high-quality information, and/or the nature of the issue makes it possible to render a solid judgment. A “high confidence” judgment is not a fact or a certainty, however, and still carries a risk of being wrong. |
|
Moderate Confidence |
Moderate confidence generally means credibly sourced and plausible information, but not of sufficient quality or corroboration to warrant a higher level of confidence |
|
Low Confidence |
Low confidence generally means questionable or implausible information was used, the information is too fragmented or poorly corroborated to make solid analytic inferences, or significant concerns or problems with sources existed |
The earliest detected attack against a Snowflake customer instance happened on April 14, 2024. The criminals used a utility, tracked as “FROSTBITE” by Mandiant, to perform reconnaissance against targeted Snowflake customers.
Want to keep informed? Sign up to our Newsletter